Overview
When users try to connect to VPN using a Domain directory account, they are getting authentication failure or timeout messages.
Local database user accounts are able to establish VPN successfully.
Debug logs are showing the following errors:
{auth} Krb5: entering auth (user: username@example.com)
{auth} kpamauth process is not responding.
{vpnclient} Client[x.x.x.x:56580](795): unable to authenticate user 'username@example.com' - authentication failed.
{vpnclient} Client[x.x.x.x:56580](795): sending ERR message, error code = 0
This article provides information on how to resolve such issues.
Solution
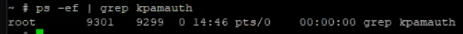
While accessing Kerio Control via SSH and searching for kpamauth process, the process is not running.
Usually, it's an indication Kerio Control is not joined to the Directory Service (Active Directory) correctly.
Moreover, in case of multiple Kerio Control firewalls connected/bonded to the AD with the same server name (default = "control"), inconsistent synchronization might happen. This can be resolved by joining the AD domain with a different name.
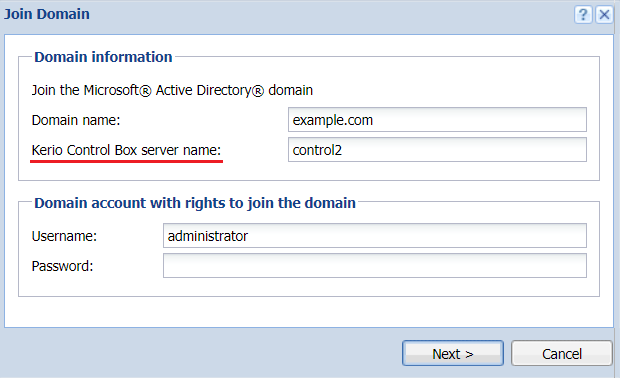
- Open Kerio Control Webadmin and navigate to Domains and User Login -> Directory Services tab.
- Click Join Domain and set Kerio Control server name to a custom value, for example, control2, kerio-site, firewall, etc.
Kerio Control Box UI
Kerio Control Software/Virtual installation
- Fill out all the necessary authorization details (username/password) and click Next to re-join the domain controller.
Testing
Ask domain users to connect using VPN, the connection should be established successfully.

Priyanka Bhotika
Comments