Overview
When the Kerio Control is joined to the Active Directory domain and there is a need to change the UPN suffix for the accounts, Kerio Control refuses to authenticate users to VPN clients. Debug logs will show similar output:
{vpnclient} Client[x.x.x.x:1029](601): unable to authenticate user 'johndoe' - authentication failed.
{vpnclient} Client[x.x.x.x:1029](601): sending ERR message, error code = 0
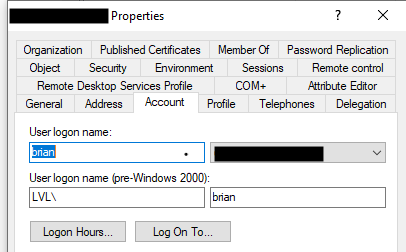
The User Principal Name (UPN) causes VPN failures, specifically, when setting up a user's Logon Name, as shown below:
Prerequisites
Kerio Control Administration access
Diagnosis
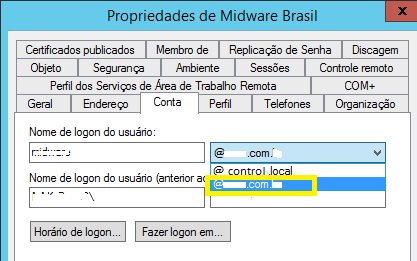
Active Directory database updates due to UPN change but the changes are not synchronized to the Kerio Control.
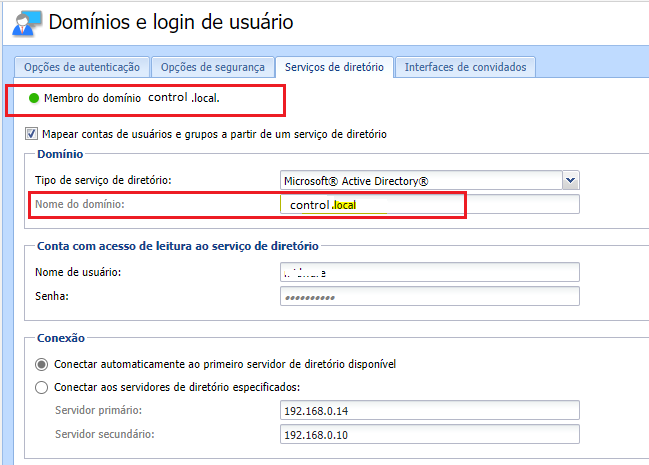
Kerio Control is a member of control.local domain
Kerio Control is aware only of control.local, so changing the UPN (to <domain>.com) can cause failed updates for the user if the Active Directory (AD) returns no response when asked for the user in question.
Solution
- Log in to Kerio Control via SSH.
- Go to the /opt/kerio/winroute directory by executing the below command:
cd /opt/kerio/winroute
-
Execute the following command:
./tinydbclient "update Ldap_v2 set ForceUsePrincipalName=0" - Restart Kerio Control.
/etc/boxinit.d/60winroute restart
Testing
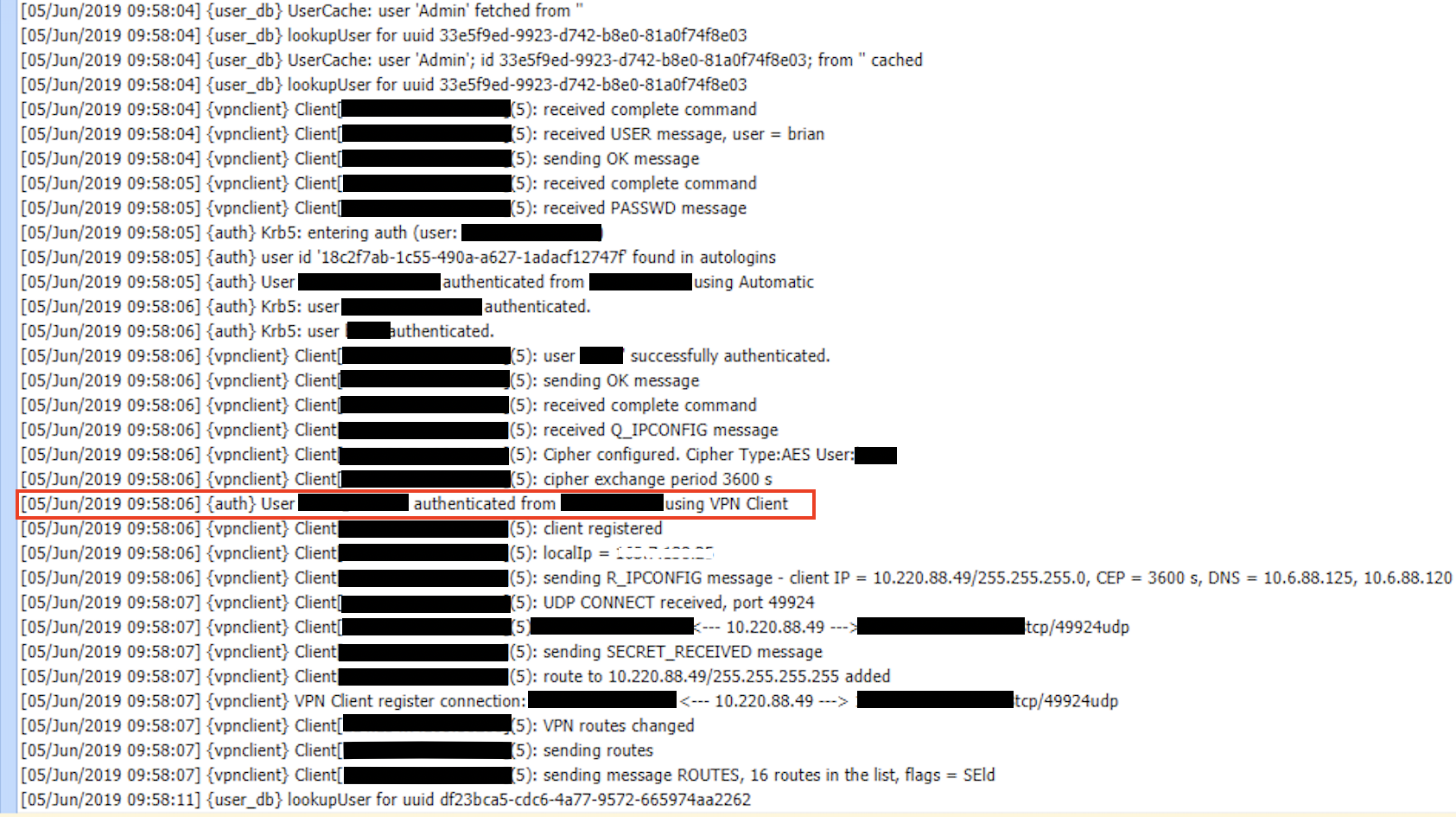
Try to connect via VPN client now. The authentication is successful. Debug logs with User database enabled will show successful LDAP username filter created: (sAMAccountName=<username>) message.
If 'User authentication' is also enabled, the following entry will appear in the debug logs:
{auth} User username@domain_name authenticated from <IP address> using VPN client
Priyanka Bhotika
Comments