Overview
Kerio Control can use NTLM (Windows NT LAN Manager) authentication to allow users to automatically log in to the firewall when they are logged onto an Active Directory or NT domain. However, if the user does not manually log out from Kerio Control, the session remains active until the session timeout period expires. This timeout period is set to 2 hours by default.
Diagnosis
If a user logs out from Windows, they do not log out from Kerio Control. The consequence of this is that a user license will continue to be in use. If administrators have more users than licenses this may prevent a new user from being able to connect through Kerio Control. Furthermore, the next user on that computer will appear to be the previous user. This may lead to incorrect logging of user activity.
It is possible to create a logout link and store it as a bookmark in order to log out from Kerio Control, or alternatively, it is possible to use some logout script to log out users automatically.
Solution
It is possible to automate the Kerio Control logout process by using a script which is called during the logout from Windows. This method will be useable for any number of users who are sharing the same machine.
In Active Directory, the Directory Controller will allow to run a script during the user's logout. This script will perform the logout automatically for the user by calling a utility that makes the necessary HTTP request to the Kerio Control's webserver for logout.
The script needs to open the URL: http://firewall_ip:4080/internal/logout
Note: the older versions are using /logout path instead of /internal/logout
- Download wget from Microsoft's page wget for Windows.
- Copy the
wget.exefile to each client's computers. - Using Active Directory, set a Group Policy to apply the
wget.exefile during the logout procedure.
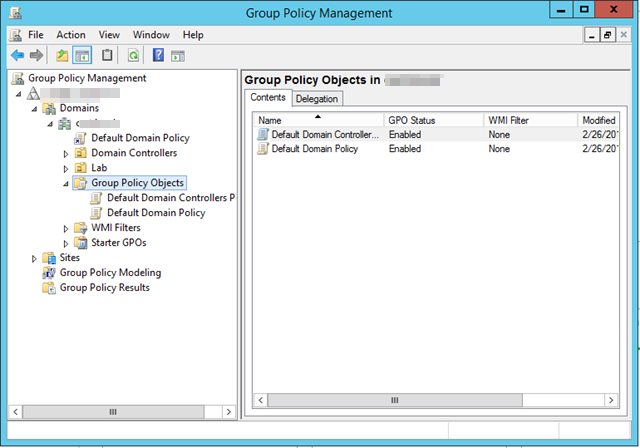
- Open Group policy settings: Active Directory Users and Groups > [your domain] > Properties > Group Policy tab, and click the Open option.
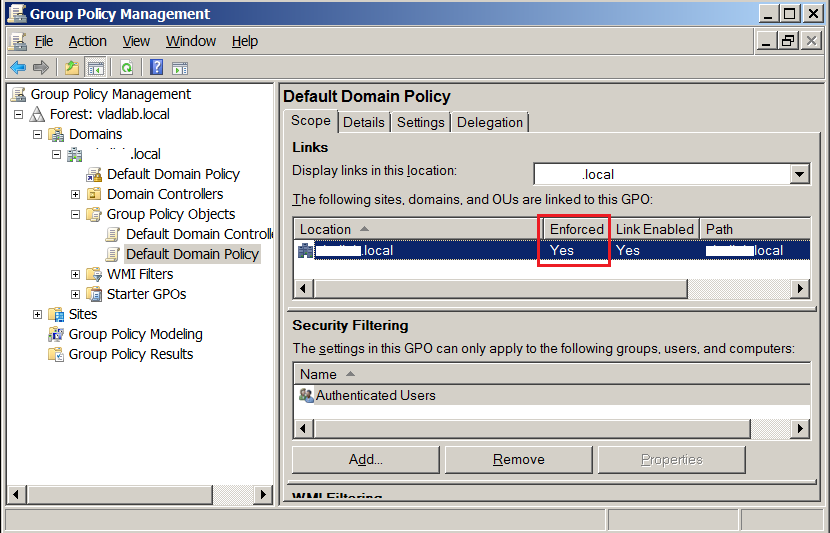
- In the Group Policy Management console, choose your domain from the left-hand menu bar. Then click Default Domain Policy under the Linked Group Policy Objects tab. Right-click and choose Edit.
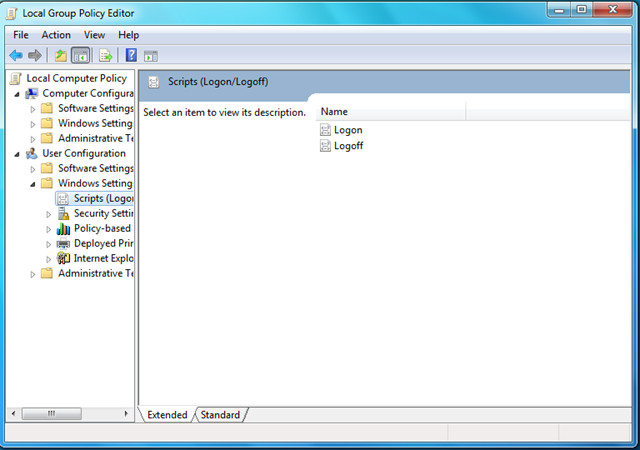
- In the Group Policy Object editor, go to User Configuration > Windows Settings > Scripts (Logon/Logoff).
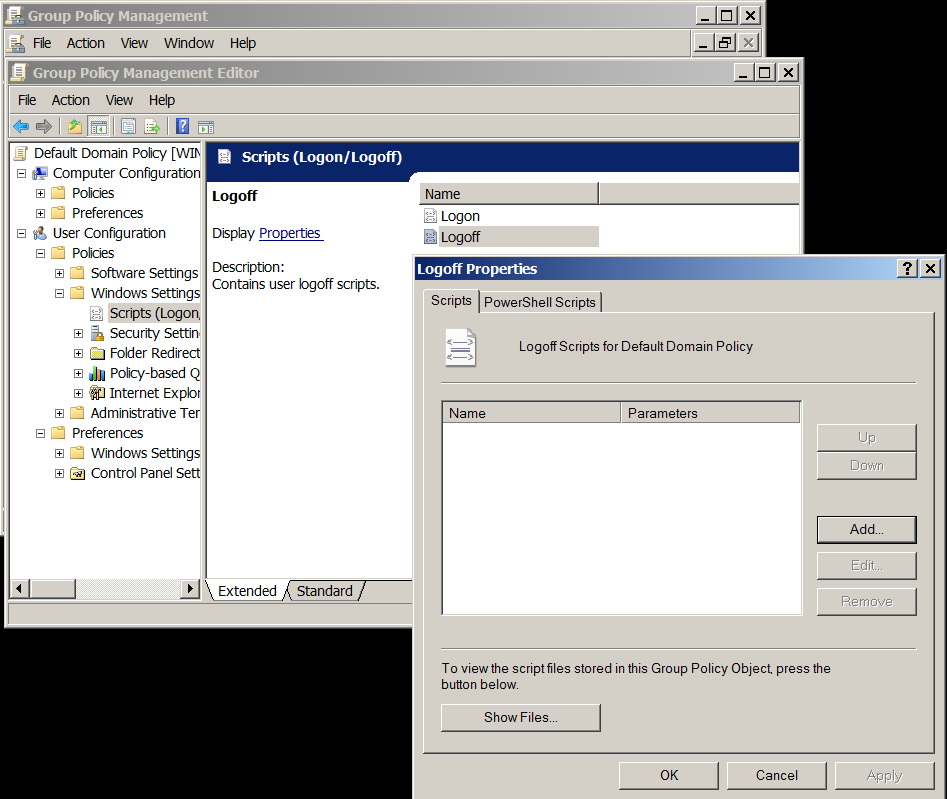
- Create a new Logoff script by double-clicking Logoff and click the Add option.
- Use these settings for your script:
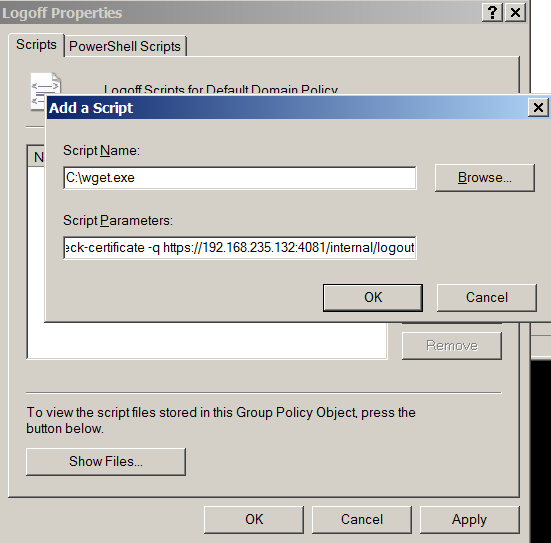
- Program/Script name:
C:\wget.exe - Program/Script parameters (http):
-q http://firewall_ip:4080/internal/logout - Program/Script parameters for https logout (server certificate is trusted):
-q https://firewall_ip:4081/internal/logout - Program/Script parameters for https logout (server certificate is not trusted, e.g. in case of self-signed certificate):
--no-check-certificate -q https://firewall_ip:4081/internal/logout
- Program/Script name:
- Save the script and exit all folders.
- Under Default Domain Policy > Properties, you must enable by checking Enforced.
Confirmation
Test the logoff script by logging a user out of windows and then checking Kerio Control to confirm the user has logged out. You can see this under Status > Hosts/Users.
Priyanka Bhotika
Comments