Overview
While users are being automatically authenticated with NTLM to the domain controller (DC) behind the Kerio Control firewall, the specific configuration should be performed. When the communication between DC and the firewall is blocked, Kerio Control might be disconnecting from the domain.
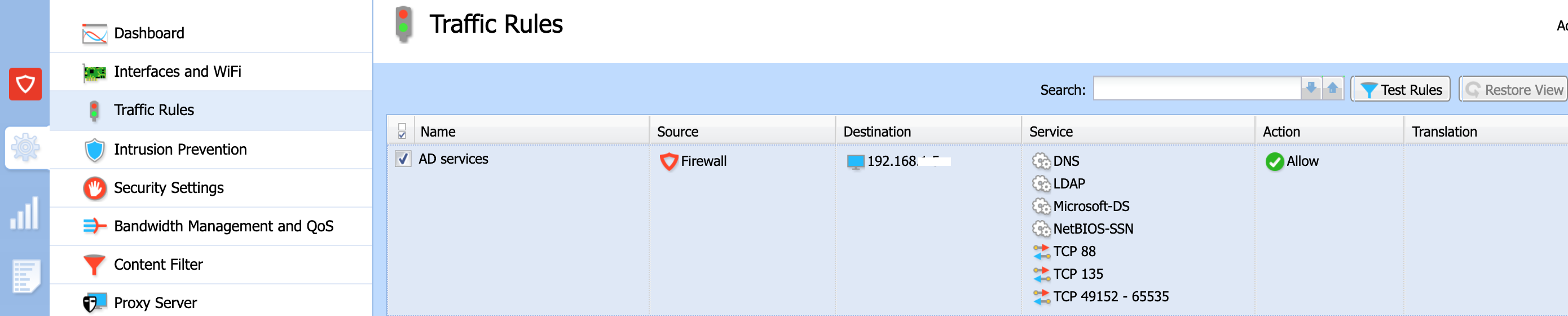
This article provides information on how to configure traffic rules allowing Windows PCs to join the domain.
Solution
To allow Windows 10 Client joining to Windows 2019 AD Domain, the following traffic rule should be configured:
Source: Firewall
Destination: <local_IP_of_DC>
Services (ports):
- DNS
- LDAP
- Microsoft-DS
- NetBIOS-SSN
- TCP 88 (Kerberos KDC)
- TCP 135 (RPC)
- TCP 49152-65535 (Randomly allocated high range TCP ports)
Action: Allow
To allow additional services, such as NTP, LDAPS, Global Catalog, etc, please refer to the 3rd-party guide Firewall Ports Required to Join AD Domain.
Priyanka Bhotika
Comments