Overview
When performing a PCI scan, the test may be failing due to SWEET32 vulnerability with the following message:
Path: /TLS server supports short block sizes SWEET32 attack
Information From Target:
Service: 4090:TCP
Server accepted TLS 1.1 64-bit block size cipher: TLS_RSA_WITH_3DES_EDE_CBC_SHA
Prerequisites
Access to:
- Kerio Control Webadmin
- Kerio Control via SSH
Process
-
Log in to Kerio Control console via SSH.
- Make the system read/writeable by running the following command:
$ mount -o rw,remount /
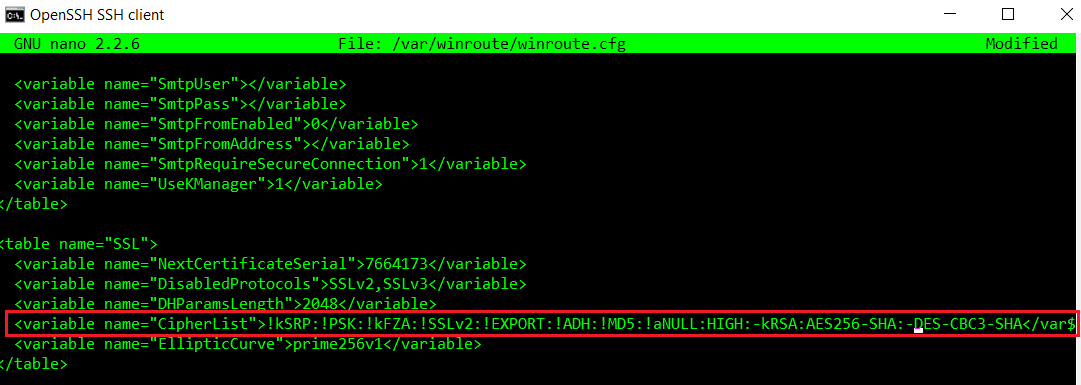
- Open the following file:
/var/winroute/winroute.cfg
- Find the table
<table name="SSL">and replace theCipherListvariable with the following line:
<variable name="CipherList">!kSRP:!PSK:!kFZA:!SSLv2:!EXPORT:!ADH:!MD5:!aNULL:HIGH:-kRSA:AES256-SHA:-DES-CBC3-SHA</variable>
As you can see,-DES-CBC3-SHAwas added at the end.
- Save changes made to the file.
- Reboot Kerio Control using the command below:
$ reboot
Note: For better security, you can disable TLS v1.0 protocol.
Confirmation
PCI scan or SSL test is completed successfully.
Priyanka Bhotika
Comments