Overview
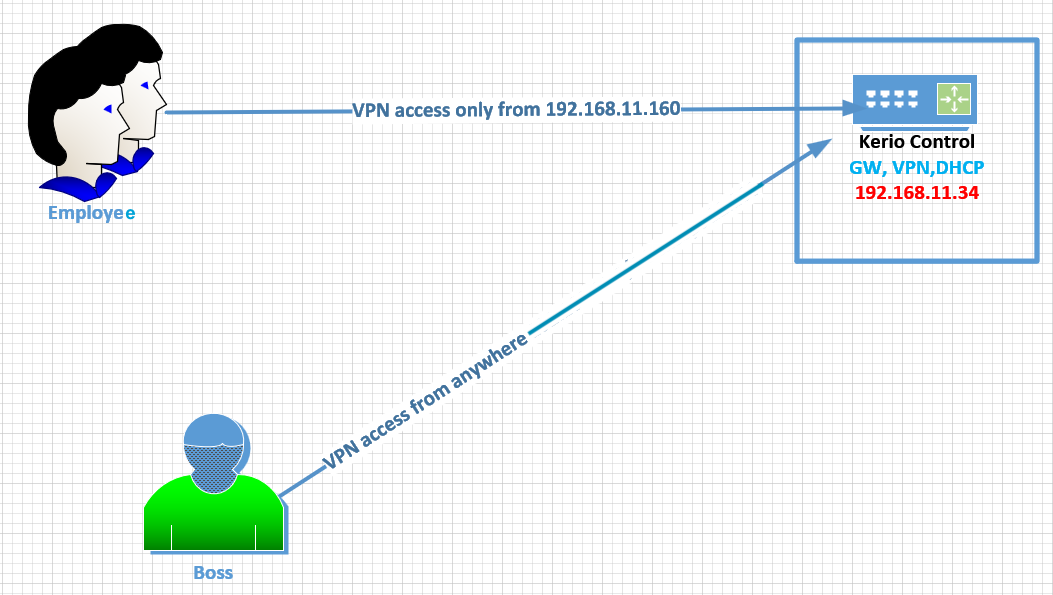
When there is a need to allow VPN access only for certain employees, connecting from a specific IP address, Kerio Control traffic rules should be configured respectively. In this particular scenario, a group of users (Employee) is using shared IP and they should be able to connect only from that IP through Kerio VPN Client. The second group (Boss, Upper Management) should have access from any IP address.
This article provides information on how to achieve such VPN restrictions requirement per IP address.
Solution
Kerio Control cannot recognize the users or groups connected from the External IP address as the source address. That's why you need to configure two separate traffic rules for restricting Employee access and use standard VPN services rule for the Upper Management group access through IPsec VPN.
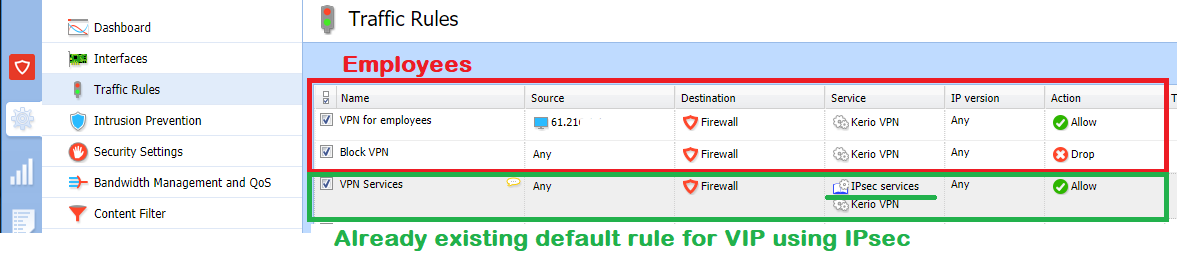
Rule VPN for employees
- Source: <public shared IP address> (192.168.11.160 is an example of test local IP)
- Destination: Firewall
- Services: Kerio VPN
- Action: Allow
Rule Block VPN
- Source: Any
- Destination: Firewall
- Services: Kerio VPN
- Action: Drop
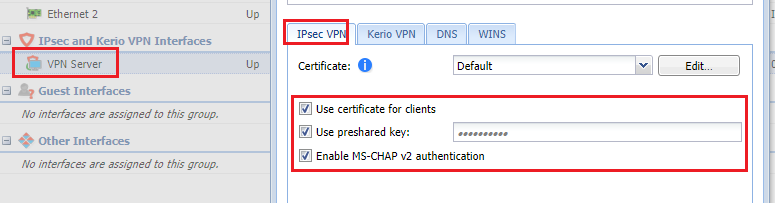
Afterward, you need to configure the IPsec VPN server with a preshared key that will only be given to the VIPs so only they can use the IPsec from anywhere.
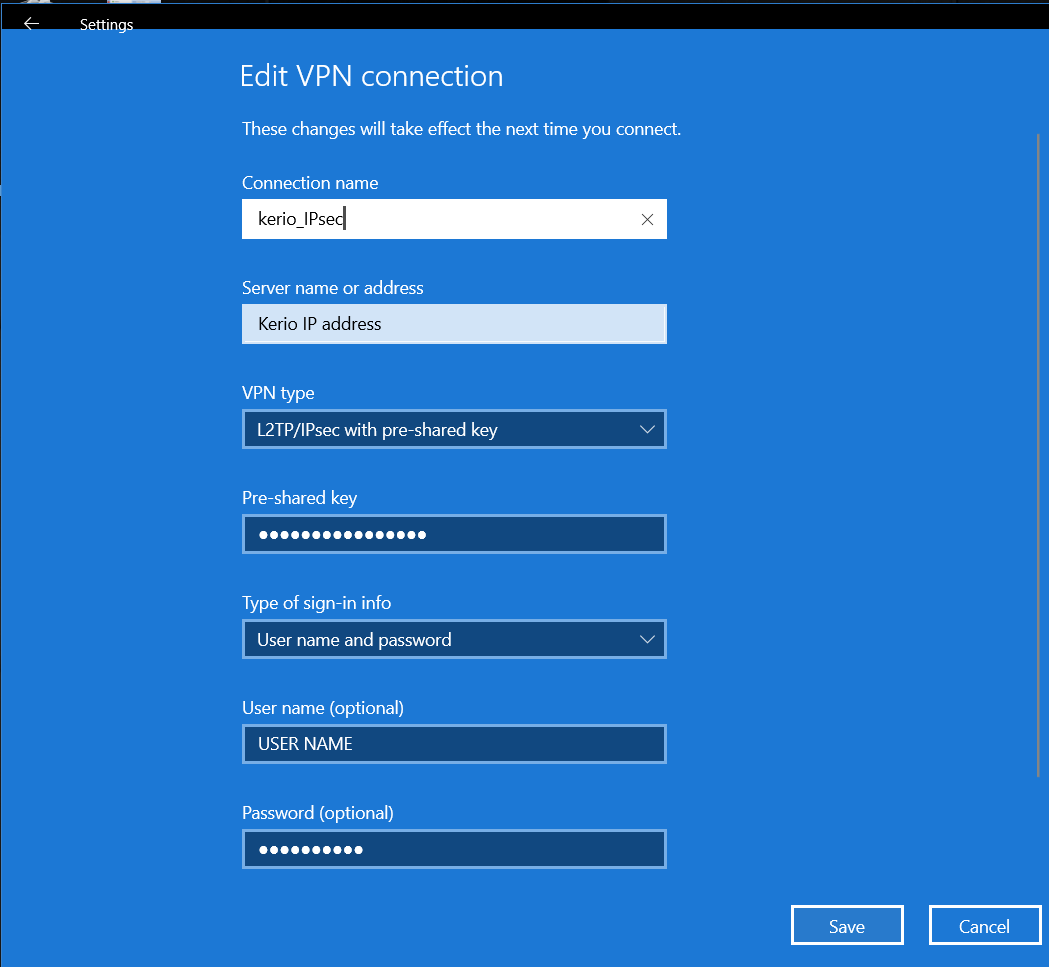
Then Upper Management can use a native IPSec VPN client on Windows or MacOS in order to connect to Kerio Control.
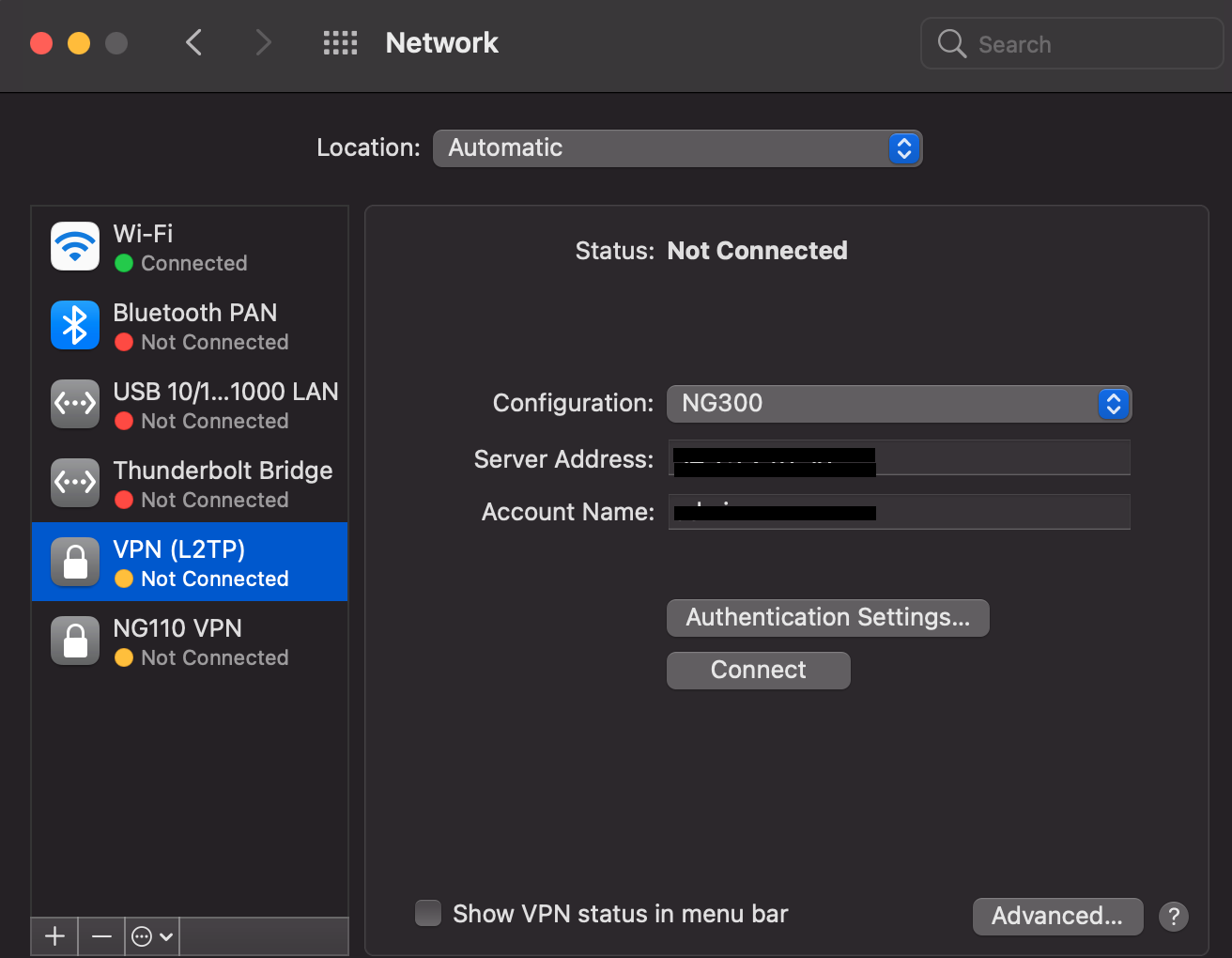
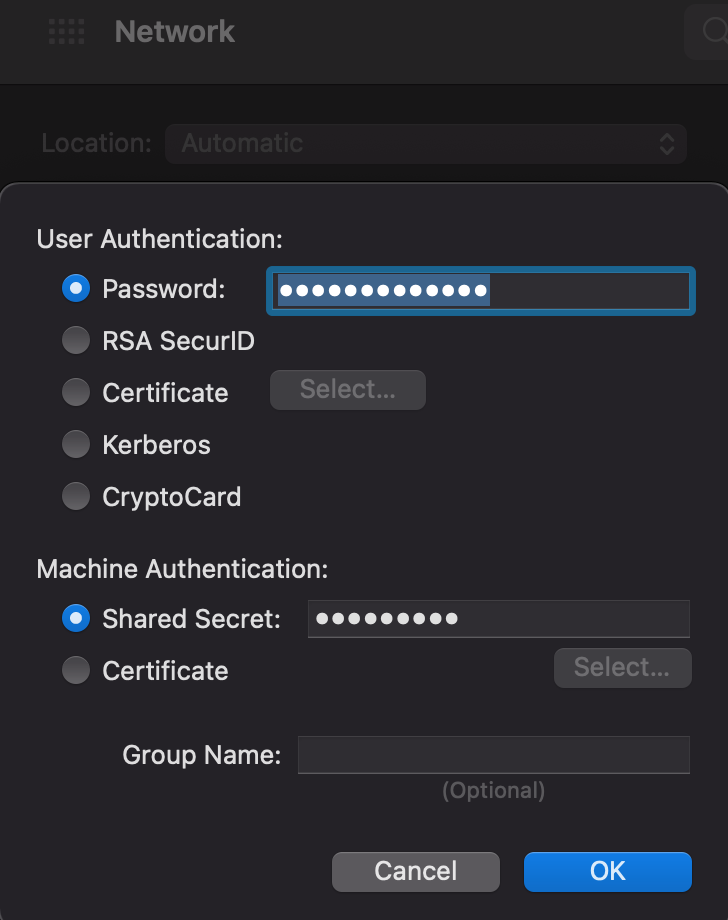
Open System Preferences > Network > Add VPN L2TP > specify the Server address and username > in the Authentication Settings window, enter the user password and Shared Secret.
Priyanka Bhotika
Comments