Overview
While trying to block all public IP addresses for the specific country, Kerio Control allows enabling GeoIP filter for incoming traffic. This filter helps you effectively stop malicious traffic and potential threats.
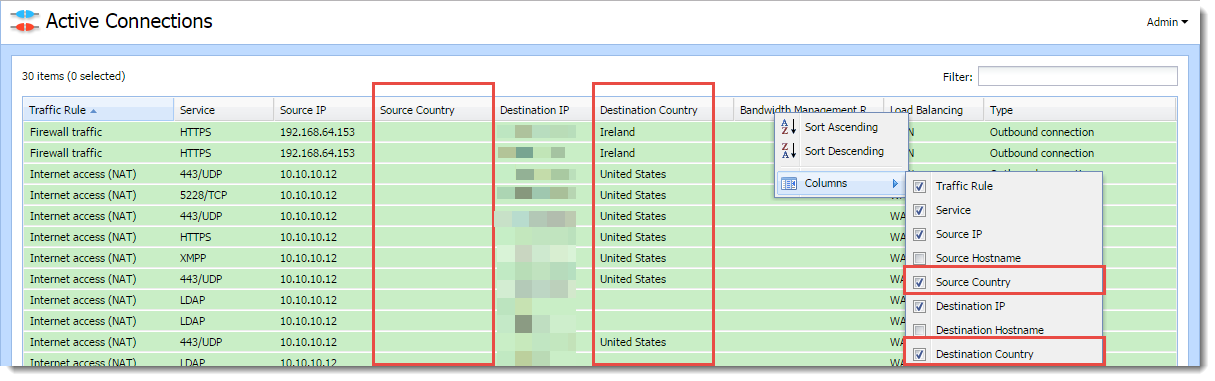
The GeoIP filter matches each IP address to its source country and displays the result in the Active Connections section. You can see any suspicious connections there and block all traffic from a given country.
Diagnosis
To display the countries associated with IP addresses in Active Connections, enable the Source Country and Destination Country columns in Active Connections:
- In the administration interface, go to Status > Active Connections.
- Right-click the table header.
- In the context menu, scroll down to Columns and select Source Country and Destination Country.
From now on, the source and destination country appear for all active connections with a nonlocal IP address.
Note: In case the Source Country and Destination Country columns are completely blank, then, you can refer to the Unable to see Source and Destination Country article to fix that.
Solution
To block all incoming connections from a specific country:
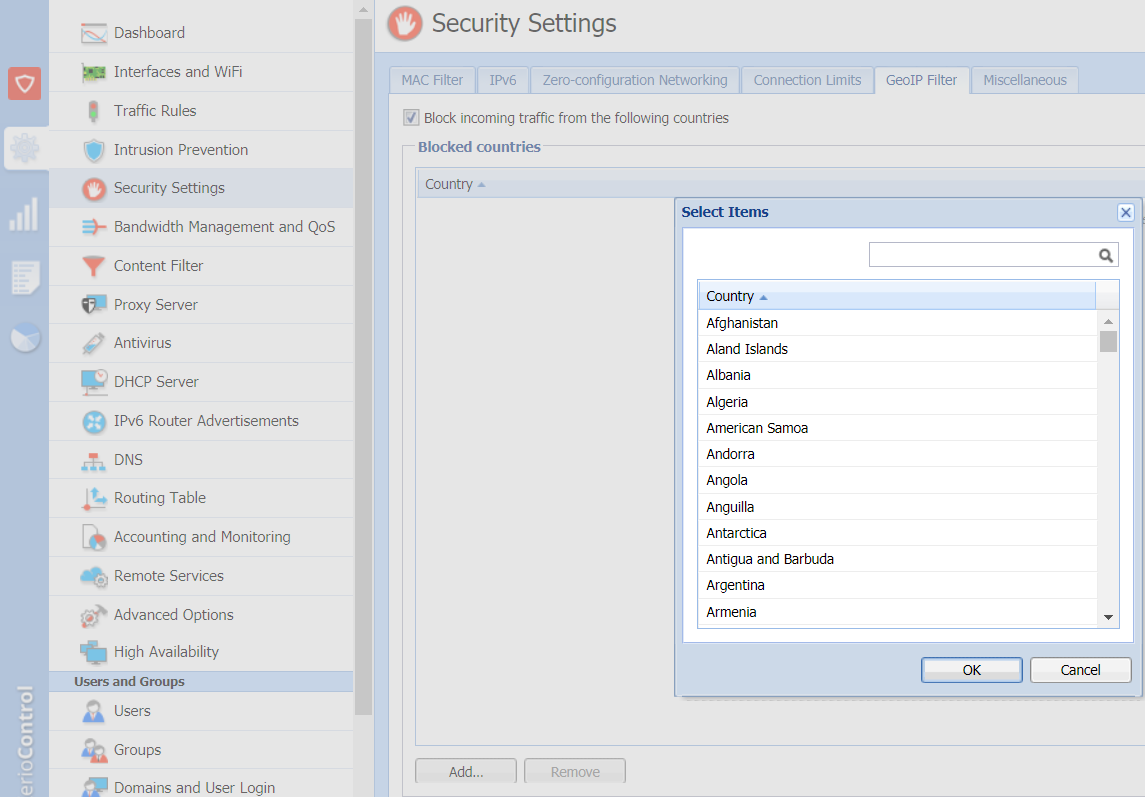
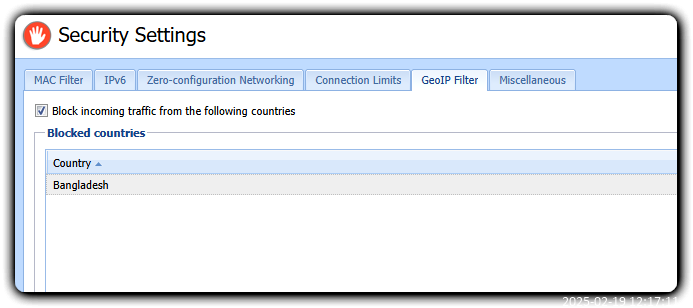
- In the administration interface, go to Security Settings > GeoIP Filter.
- Verify that the Block incoming traffic from the following countries option is enabled.
- Click Add.
- In the Select Items dialog box, select the countries you want to block.
- Click OK.
- Click Apply.
From now on, Kerio Control blocks all incoming connections from the selected countries. Outgoing connections are allowed.
Whitelist Specific Addresses from Blocked Country
The GeoIP filter in Kerio Control operates with the highest priority, meaning it takes precedence over all traffic rules, content filters, and other security settings. If a country is blocked using the GeoIP filter, all IP addresses from that country will be denied access, and it is not possible to create a whitelist using traffic rules or content filtering.
💡New in Kerio Control 9.4.5 p1: you now have the ability to create GeoIP address groups and leverage them in your traffic rules in order to implement a whitelist! See the full details in the dedicated Kerio Control GeoIP User Guide. Note that the GeoIP address groups leveraged in the traffic rules are not depending on the enablement of the GeoIP filter, allowing you full flexibility.
Therefore, in order to implement your GeoIP in whitelist in Kerio Control 9.4.5 p1 and later, you would need to follow the below steps (proof of concept for denying US traffic)
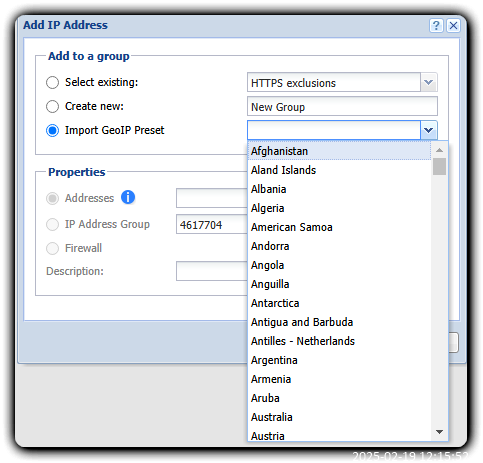
- Define your GeoIP address groups:
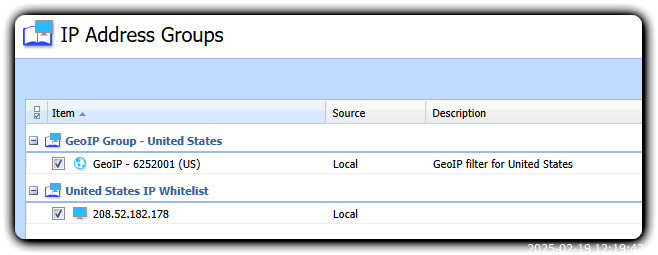
- Define as well your desired IP whitelist group, so that you wind up with something like this:
- Go to Security Settings > GeoIP Filter and remove the US from the list (or disable the GeoIP flag if you don't need other countries fully blocked)
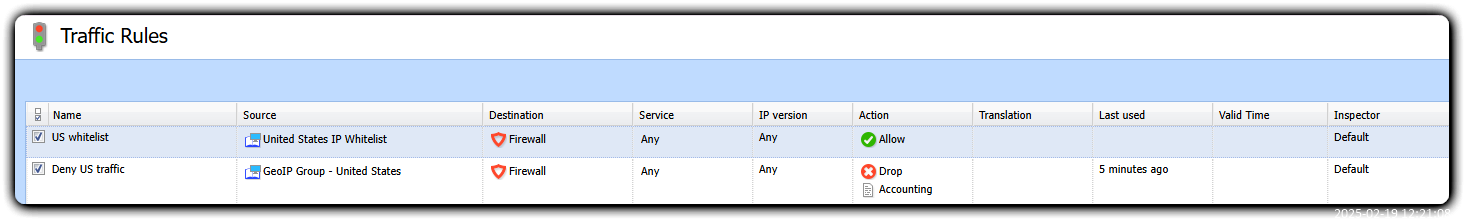
- Navigate to Configuration > Traffic Rules, and configure 2 traffic rules:
- A whitelist rule sitting at the top - this is where you would input your whitelist IP address group as the Source, with Destination Firewall and Action ALLOW
- A block rule below it, where you would input the GeoIP address group for US as the Source,
- Source, with Destination Firewall and Action DROP or DENY
This way, all US traffic will be blocked, except for the IP addresses that you designated in the whitelist.
Testing
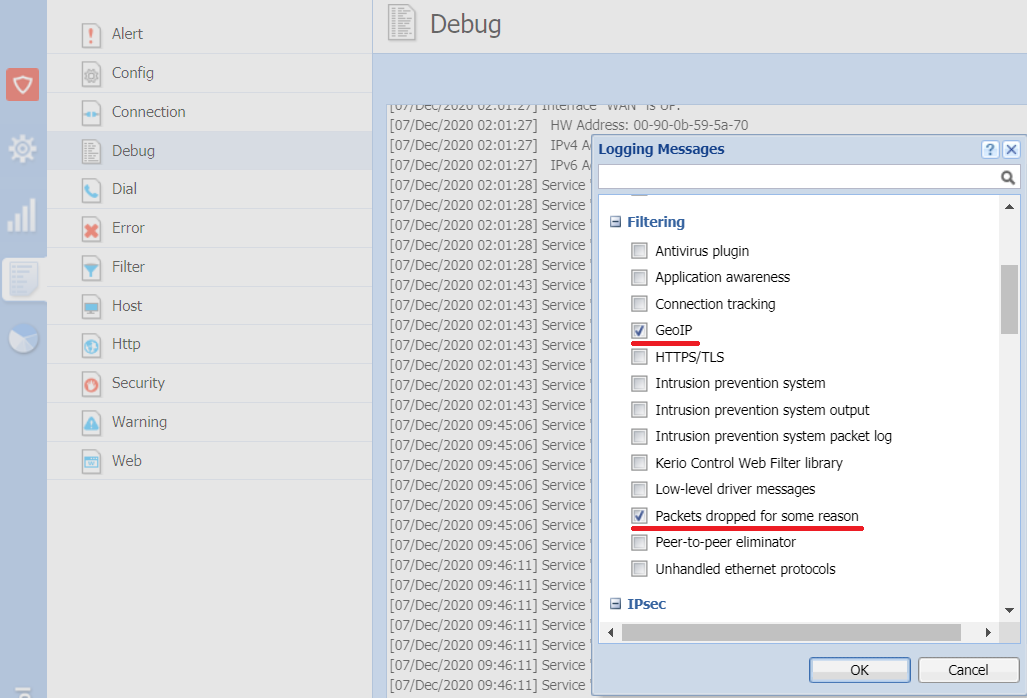
To verify which packets are dropped by Kerio Control, use the Debug log:
- In the administration interface, go to Logs > Debug.
- Right-click to the log window.
- In the context menu, click Messages.
- In the Logging Messages dialog box, select GeoIP and Packets dropped for some reason.
- Click OK.
Important: disable Debug options once the verification is completed so it won't affect overall performance.
Priyanka Bhotika
Comments